1C Cloud. Requirements for reports and external processing
Developer Guide / For 1C Cloud account owners / 1C Cloud. Requirements for external processing1C Cloud. Requirements for reports and external processing
This article provides requirements for additional reports and processing that must work in the service model.
1. In the e-Cont.md service, compliance with the requirements described in this article is checked by 1C employees during an audit, which additional reports and processing must successfully pass in order to be allowed to use in the service.
2. We recommend that you read the article about the most common errors and difficulties in preparing configuration extensions, additional reports and processing.
Contents
6. Requirements for data transfer outside the service
9. Methodological recommendations
9.1. Examples of additional reports and processing
9.2. Development recommendations
9.3. Metadata names of an additional report or processing
9.4. About copying code from a standard configuration
9.5. Working with the database
9.6. Working in the web client
1. General requirements
- An additional report or processing is created on the developer's local computer using the 1C:Enterprise 8 configurator as external reports and processing and saved to a file. The standard extension of this file name is:
- epf — for additional processing;
- erf — for additional reports.
- An additional report or processing intended for operation in the e-Cont.md cloud technology service model must be developed in accordance with the requirements of the AdditionalReportsAndProcessings subsystem of the standard subsystems (SSL). You can read more about these requirements here and here.
- For additional reporting or processing, the standards and methods for developing configurations for the 1C:Enterprise technological platform must be followed 8", available via link.
2. Using Safe Mode
- In the ExternalProcessingInfo() function of the additional report or processing object module, the RegistrationParameters.SafeMode parameter must be set to True.
- If you need to use operations in an additional report or processing that are not allowed in safe mode, you should request the necessary permissions in the ExternalProcessingInfo function using function calls:
as shown in the processing _DemoLoadingItemsFromPriceListSecurityProfiles from the Demo configuration "Library of standard subsystems" version 2.4. For descriptions of the above functions, see by link.РаботаВБезопасномРежиме.РазрешениеНаИспользованиеВнешнегоМодуляРаботаВБезопасномРежиме.РазрешениеНаИспользованиеВнешнейКомпонентыРаботаВБезопасномРежиме.РазрешениеНаИспользованиеИнтернетРесурсаРаботаВБезопасномРежиме.РазрешениеНаИспользованиеКаталогаВременныхФайловРаботаВБезопасномРежиме.РазрешениеНаИспользованиеКаталогаПрограммыРаботаВБезопасномРежиме.РазрешениеНаИспользованиеКаталогаФайловойСистемыРаботаВБезопасномРежиме.РазрешениеНаИспользованиеПривилегированногоРежимаРаботаВБезопасномРежиме.РазрешениеНаИспользованиеПриложенияОперационнойСистемыРаботаВБезопасномРежиме.РазрешениеНаСозданиеCOMКласса
WorkingInSafeMode.PermissionToUseExternalModuleWorkingInSafeMode.PermissionToUseExternalComponentWorkingInSafeMode.PermissionToUseInternetResourceRunningInSafeMode.PermissionToUseTemporaryFilesDirectoryRunningInSafeMode.PermissionToUseProgramDirectoryRunningInSafeMode.PermissionToUseFileSystemDirectoryRunningInSafeMode.PermissionToUsePrivilegedModeRunningInSafeMode.PermissionToUseOperatingSystemApplicationRunningInSafeMode.PermissionToCreateCOMClass
- Code execution by third parties is not allowed, i.e. by means that are not part of the configuration.
- It is not allowed to use COM objects, since they will not function on the service's production servers running Linux.
- It is allowed to use only external components that are included in the configuration for which the additional report/processing has been developed as mock-ups.
3. Requirements for conducting an audit
- It is not allowed to use any means that complicate or make impossible the analysis of the source texts of the additional report or processing modules. In particular, it is not allowed to:
- deliver modules without source code or with a password set for the module;
- use means of obfuscation of source code.
4. Resource requirements
- Additional report/processing should not lead to excessive load on service components or client application.
- Limits for each server call in additional report or processing in e-Cont.md service:
If the limit is exceeded, the server call is interrupted (but the session itself continues to live).Parameter Limit value Server call duration 2 400 sec Server call CPU time 600 sec DBMS call duration 1,200 sec Service call duration 600 sec Memory used 4,194,304 KB Amount of information written to disk 20,971,520 KB
5. Performance requirements
- An additional report or processing must not disrupt the correct operation of the application in which it is installed.
- All long operations in an additional report or processing must use the long operations mechanism from the BSP (if the duration is 10 seconds or more).
- If an additional report or processing is intended only for use in a thin client, then when launched in a web client it must correctly notify the user of this limitation, and not terminate with errors.
6. Requirements for data transfer outside the service
- If any data is transferred outside the service in an additional report or processing, these operations must be confirmed by the user.
- If it is possible to determine the Internet resources to be accessed at the stage of developing an additional report or processing, it is necessary to implement a permission request in the program interface of the additional report or processing. Such a request should enable the user to see which resources will be accessed by this report or processing before installing the report or processing.
- If it is impossible to determine the Internet resources to be accessed, then:
- for additional reports or processings containing forms, permission should be requested from the user before performing the operation (possibly with saving the received response). When requesting permission, you should clearly indicate which Internet resources will be accessed;
- for additional reports/processes that do not contain forms (for example, intended for use as a scheduled task), it is recommended to:
- by default, do not perform the operation in the server command code;
- create an additional command with the call type Opening a form, in which to implement the confirmation request;
- start performing the operation in the server code only after the user confirms the execution of the operations.
7. Legal Requirements
The additional report or processing must not contain:
- Code that may cause data corruption or destabilize the service.
- Code and data that may violate the rights of third parties, including their copyright.
- Information protected by law, including trade secrets or personal data of third parties.
8. Testing Requirements
Once the additional report or processing is developed, the developer must test it. To check, you need to:
- Deploy the 1C:Enterprise 8 server of the same version that is used in the service.
- Deploy the client-server infobase of the configuration for which the additional report or processing is intended, and of the configuration version that is used in the service.
- Perform a web publication of this infobase (except for the case when the additional report or processing is intended only for work in the thin client).
- For each user profile under which the additional report or processing will be executed in the service model, you must create a user in the infobase with the same set of roles, but without the SystemAdministrator role (this role is not allowed for regular, i.e. separated, users when working in the service model).
- Run the additional report or processing in the thin client and in the web client (if the additional report or processing contains forms, except for the case when the additional report or processing is intended only for work in the thin client), under the users created in p. 4. To start, use not the main menu (the File — Open command), but the interface of additional reports and BSP processing.
For each user created in p. 4, it is necessary to check:
- whether the additional report or processing is loaded into the local information base at all;
- the functionality embedded in the additional report or processing is working and executed correctly.
9. Methodological recommendations
9.1. Examples of additional reports and processing
Examples of additional reports and processing can be obtained:
- In the article following the link.
- In the demo information base of the BSP:
- by opening it in 1C:Enterprise mode — in the Additional reports and processing directory;
- by opening it with the Configurator — in the General / General layouts configuration branch (for example, _DemoFillingCounterparties, _DemoReportOnInvoicesForPaymentGlobal, etc.
If necessary, you can save these examples to files and develop additional reports and processing based on them.
9.2. Development Recommendations
- When developing an additional report or processing, it is recommended to use:
- the same version of the 1C:Enterprise 8 platform that is used in the service;
- the same version of the configuration of the application solution for which the additional report or processing used in the service is being developed;
- the library of standard subsystems (LSS) of the version that is implemented in the used version of the configuration of the application solution, or a newer one. You can download the BSP versions via the link.
- Use the BSP programming interface and application configurations. In this case, you will not have to rewrite the code of an additional report or processing each time after updating the standard configurations.
- If an additional report or processing contains forms, "keep" them in the style of the standard configuration. For example, if the configuration requires the "Save and Close" command to be placed at the top of the form, do not place it at the bottom of the additional report or processing form.
- Comply with development standards (see by link).
9.3. Names of additional report or processing metadata
- When developing additional reports and processing for the service model, it should be taken into account that the name of the additional report and processing metadata can be arbitrary, and accordingly, the full names of all forms of the additional report and processing.
- You can get the name of the metadata object on the server using the method FormAttributeToValue(NameOfMainAttribute).Metadata().FullName()
- If, when working in the service model, an error Unknown form name occurs when opening a child form of an additional report or processing, this is most likely due to the incorrect use of form names in the additional report or processing.
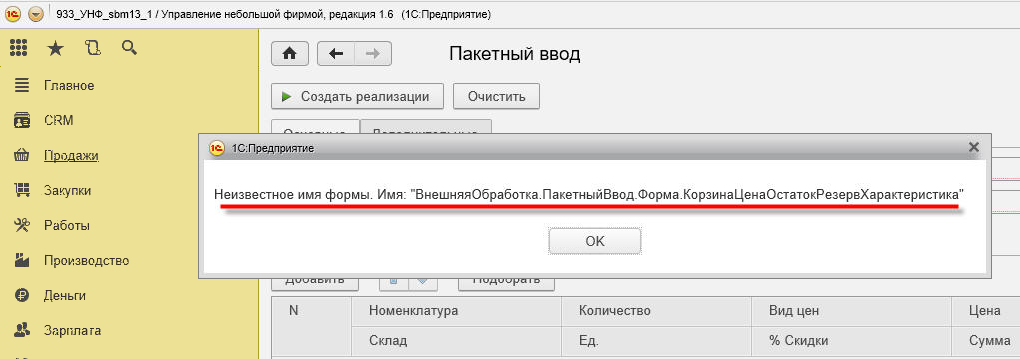
9.4. About copying code from a standard configuration
- If the standard configuration has a ready-made function that can be called, you do not need to copy it to an additional report or processing.
- If the code in the standard configuration is not completely suitable, be very careful when copying existing code:
- if an error is detected and corrected in the copied code, this error will not be corrected for users of the additional report or processing. In this case, you take responsibility for timely error correction for users;
- as the configuration develops, previously copied code can corrupt user data.
9.5. Working with the database
- When changing several data elements in a related manner that must occur atomically, use transactions.
- When changing data that can be edited by users in parallel with the execution of an additional report or processing, set object locks.
- Be sure to pay attention to the optimality of queries: keep in mind that, unlike the local mode, the information base in the service is used by a large number of users. For more information on query optimization, see the 1C:ITS articles by link.
9.6. Working in the web client
- If actions on the server can take a long time, use the BSP long-running operations mechanism. Otherwise, the application may close due to a web server timeout error.
- If an additional report or processing can be called while working in a web client, then all key features of the additional report or processing must be available to users without using a file extension.
9.7. About the security of user data
- Do not provide the end user with such processing, with which he can corrupt the data in his application. Examples:
- universal "renumberers" and "reprefixers";
- search and replace values;
- universal editors of attribute values;
- deletion of marked objects without reference integrity control.
- It is advisable to clearly limit the functionality of additional processing that changes user data. For example, if the user needs to renumber cash documents, create an additional processing that will do exactly this, without unnecessary universality.



