1C Cloud. Recommendations for preparing configuration extensions, additional reports and processing
Developer Guide / For 1C Cloud account owners / 1C Cloud. Recommendations for preparing configuration extensions, additional reports and processing1C Cloud. Recommendations for preparing configuration extensions, additional reports and processing
This article provides advice on how to prepare configuration extensions, additional reports, and processing for use in the service to ensure their proper quality and to help them pass audits quickly.
Contents
1. Recommendations for preparing configuration extensions
2. Recommendations for preparing additional reports and processing
3. How to use methods prohibited in safe mode
5. Universal Processing and Extensions
1. Recommendations for Preparing Configuration Extensions
1.1. Main reasons for failure
In configuration extensions that fail the audit, in most cases it is found that:
- The extension is not intended to run in secure mode.
- The extension is not prepared for use in the service.
- The extension version is not specified.
- The configuration extension that extends data is used in configurations that do not yet support this feature.
1.2. Features of configuration extensions
- The extension must have a unique name and extension version.
- Development must be performed on the same platform version.
- Adaptation to secure mode and data separation mode is required.
1.3. Useful information
- It is necessary to comply with the requirements specified in the Developer's Guide "1C:Enterprise 8.3": chapter "Configuration extension" (see follow the link).
- If the extension contains forms, the developer must ensure their functionality in the web client under all web browsers supported by the technological platform "1C:Enterprise 8".
2. Recommendations for preparing additional reports and processing
2.1. Main reasons for failure
In additional reports and processing that did not pass the audit, in most cases it is found that:
- The additional report or processing is incorrectly connected to the BSP.
- The additional report or processing is not intended to be executed in secure mode.
- The additional report or processing is not prepared for use in the service.
- There is an incorrect call to the additional report/processing from the code.
2.2. Connecting an additional report/processing to the BSP
Registration of an additional report or processing in the information base occurs based on the registration parameters supplied by the report/processing. These registration parameters must be formed in the form of a structure as a result of executing the function Information About External Processing of the report/processing module:
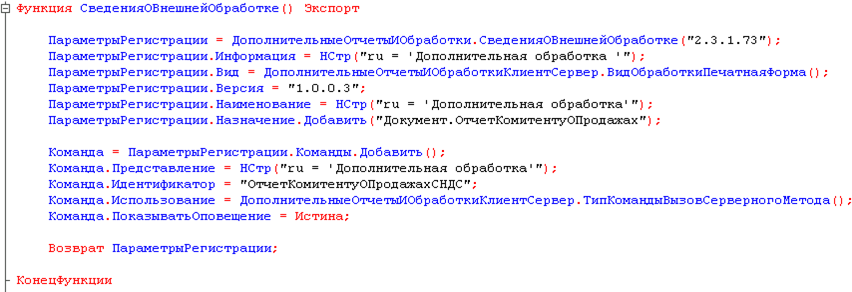
A description of the fields of the registration parameter structure is provided in the BSP documentation link.
Registration parameters include a table of commands supplied by the additional report (additional processing):
- for global additional reports/processings, these commands are placed in the global command interface;
- for assigned additional reports/processings, these commands are placed in the context of the objects for which they are intended, while the registration parameters of the additional report/processing must specify the target objects (an array of metadata object name strings).
The type of additional report/processing, the type of use of the supplied commands must correspond to the concept of the additional report/processing.
2.3. Accessing an additional report/processing from code
Please note that you cannot access an additional report/processing by name, for example:
<big>ExternalProcessing.Re-postDocumentsSequentially</big>The additional report/processing is connected to an information base with a different name (unique identifier). Therefore, to generate a request to an additional report/processing, you should define the full name of the connected report/processing in the handler OnCreationOnServer as follows:
<big>FullNameOfObject = FormAttributeToValue("Object").Metadata().FullName();</big>And then request the additional report/processing as follows:
<big>FullNameOfObject + ".RepostDocuments"</big>
2.4. Debugging an additional report/processing
When debugging an additional report or processing, do not open it through the main menu: File — Open, but through the interface of the subsystem of additional reports and processing of the BSP.
Open and test the processing not with administrator rights, but with a set of rights of those users who will use the processing.
3. How to use methods prohibited in safe mode
3.1. Safe mode
All configuration extensions, additional reports/processing are performed in the service in safe mode using security profiles.
The following operations are prohibited in safe mode:
- Executing the methods Run() and Calculate()
- Privileged mode
- Working with external components
- Working with the file system, except for temporary files
- Working with operating system applications
- COM objects (server code can be executed on Linux, we cannot guarantee the presence of COM objects on the server)
- Access to the Internet, etc.
For more information about safe mode, see the documentation for "1C:Enterprise" by link.
3.2. Security profiles
Some actions prohibited in safe mode can be allowed using security profiles.
A security profile is a set of explicitly defined permissions to perform certain actions, which can be assigned to infobases, configuration extensions, additional reports and processing. Security profiles are stored in the 1C:Enterprise server cluster.
Security profiles are automatically generated (if necessary) for configuration extensions, additional reports, and processing loaded into the service:
- for configuration extensions — based on requests for permission to perform unsafe actions specified when loading the extension into the service, as well as the results of automatic verification of the configuration extension;
- for additional reports and configuration processing — based on requests for permission to perform unsafe actions specified in the ExternalProcessingInformation function of the additional report or processing.
For more information about security profiles, see the documentation for "1C:Enterprise" by the link and in the Security Profiles sections of the chapters "Configuring and Using Subsystems When Developing a Configuration" and "Programming Interface" of the Standard Subsystem Library (SSL) documentation, see here and here.
3.3. What unsafe methods can and cannot be used
In configuration extensions, additional reports and processing intended for use in the e-Cont.md service, the following unsafe operations can be used:
- access to the temporary files directory (read and/or write);
- access to Internet resources;
- privileged mode;
- access to external components, included in the configuration for which the configuration extension, additional report or processing is developed.
It is prohibited to use:
- access to the file system (except for access to the temporary files directory);
- access to COM objects (since the server code may run on Linux, we cannot guarantee the presence of COM objects on the server);
- access to external components that are not part of the configuration for which the configuration extension, additional report, or processing is developed;
- operating system applications;
- server-side cryptography tools.< /li>
Please note that unsafe operations are prohibited only on the server!
3.4. Requesting permissions for configuration extensions
If a configuration extension uses operations that are not allowed in safe mode, then when loading the extension version into the service, you must specify the necessary permissions to perform unsafe operations (for more details, see the article via link):
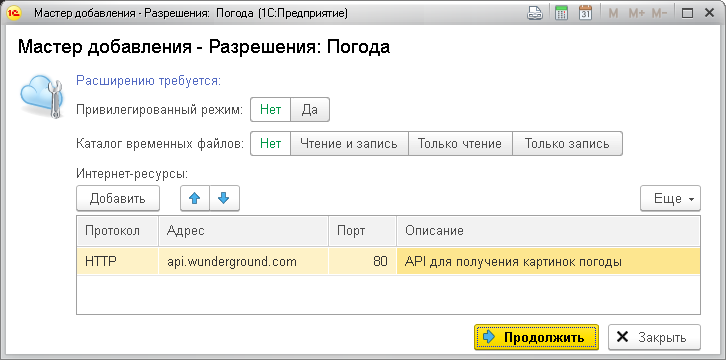
You do not need to request permissions to access external components included in the configuration; they will be granted automatically.
3.5. Requesting permissions for additional reports and processing
If you need to use operations in an additional report or processing that are not allowed in safe mode:
- Request the necessary permissions in the ExternalProcessingDetails function of the additional report or processing using function calls:
<big>WorkingInSafeMode.PermissionToUseExternalComponent</big><big>WorkingInSafeMode.PermissionToUseInternetResource</big>
- In the function InformationAboutExternalProcessing of an additional report or processing, specify the operating mode of the additional report or processing Safe .
4. Performance Considerations
Configuration extensions, additional reports and processing should not cause degradation of service performance. Therefore, the queries used in the built-in language must be optimally constructed and comply with standards (for more details, see here and here ). Typical reasons for non-optimal query performance and methods for query optimization are discussed in the article 1C:ITS by link.
Particular attention should be paid to optimizing:
- joins with virtual tables, subqueries (they can lead to a significant slowdown in the query);
- selections with "OR";
- queries with by retrieving data through a dot from fields of a composite reference type (when executing such a query, a join will be performed with all tables of objects included in the composite type).
Common refusal formulations:
- The query is not constructed optimally.
- You must follow the recommendations of https://its.1c.ru/db/metod8dev/content/5842/hdoc.
When writing a configuration extension, additional report and processing, you must avoid code that can lead to unreasonably increased consumption of processor time. First of all, this concerns “empty” cycles:

5. Universal processing and extensions
You should avoid universal configuration extensions, additional processing, especially if they can change user data. You should create extensions and processing aimed at solving specific problems. Universal extensions and handlers are dangerous for the following reasons:
- their use may require a high level of user qualification, which cannot be guaranteed;
- the user may change the details of service objects or objects that he did not intend to change;
- the business logic of the application solution may be violated.
Common refusal formulations:
- We cannot allow the use of universal handlers, since their use requires a high level of user qualification, which cannot be guaranteed.
6. Using temporary files
When accessing temporary files, you must follow the requirements of the standards described at the link. In particular, it is incorrect to write:
<big>TempFile = "/tmp/temx.txt"</big>Correct:
<big>TempFile = GetTempFileName("txt")</big>In this case:
- the uniqueness of the temporary file name is guaranteed;
- automatic cleaning is performed when the workflow is restarted.
It is also necessary to ensure that temporary files are deleted after use.
Common refusal formulations:
- To get the name of the temporary file, you must use the GetTemporaryFileName() method;
- You must delete temporary files after use.
7. Other issues
When developing configuration extensions, additional reports and processing, the following requirements must be taken into account.
- Long-term operations must be performed in the background (for more details, see here and here).
- If user data leaves the service, the user must consent to this.
- The standard logic of application solutions (configurations). Do not disable standard mechanisms and checks, for example, using constructions like:
<big>DataExchange.Loading = True</big> - Do not hide system information about errors received in the Attempt' — Exception operator from the user. Without this information, it will be much more difficult for the service support service to understand the causes of the error.



